It looks like human nature strikes again. PayPal recently announced attackers succeeded with credential stuffing attacks on nearly 35,000 PayPal accounts. The widely used financial app notified its compromised clients to immediately change their PayPal passwords. The company found that the attack was limited to account holders only, and their own data systems were not breached in any way.
According to PayPal, a bad actor accessed customer accounts by credential stuffing passwords compromised in prior data breaches having nothing to do with PayPal. They say one of the most consequential, basic mistakes of account protection – reusing the same password for more than one account, enabled the attacks.
The Effects of Credential Stuffing
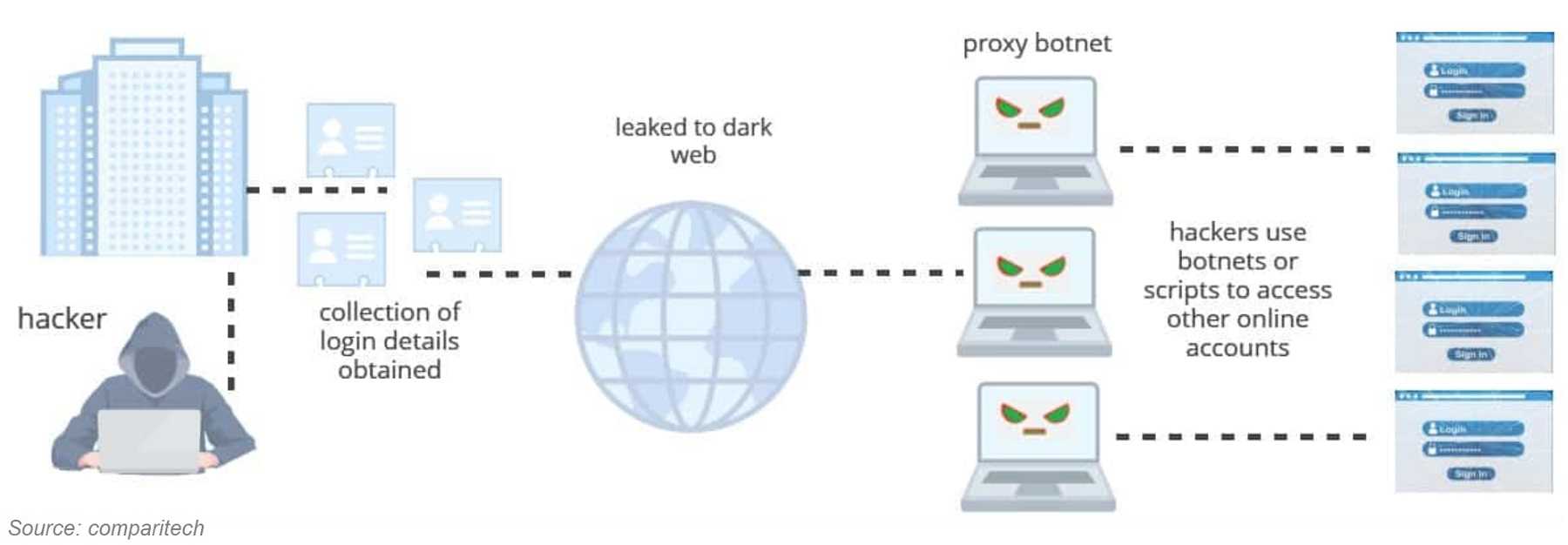
Credential stuffing, at its core, uses passwords and other PII already compromised through hacking or data breach incidents. As a result, hijacked passwords and other identifying info like name, email address, online accounts, and more end up in the wrong hands.
While some thieves sell the pilfered PII on the dark web, others post it for free. Either way, compromised passwords then get crammed into account login pages until a reused password match is made. From there, criminals have unfettered access to accounts, enabling further crimes like financial and identity theft.
The PayPal attacks found exactly 34,942 account password matches, leading PayPal to temporarily change the affected passwords themselves. It’s their decision to help limit the credential stuffing until compromised users create their own new, strong, and unique passwords.
Repeat Offenders Pay the Price
Unfortunately, we know by now that human nature leads to password reuse. After all, doesn’t using your birthdate, address, phone number, or other PII guarantee you’ll remember it? And who needs all those pesky, long passwords when a one-size-fits-all approach does the trick? It’s time for “repeat offenders” to get realistic about reusing passwords and the enormous risk they do to their own online security.
Just a reminder…passwords should be 8 characters long or more. In addition to making them unique for every account, using a mix of upper- and lower-case letters and special characters is recommended. Finally, never use whole words, phrases, or special dates like birthdays and anniversaries. They’re too predictable and hackers count on them for success. Remember, you have the power to create secure passwords, so don’t wait until it’s too late.

