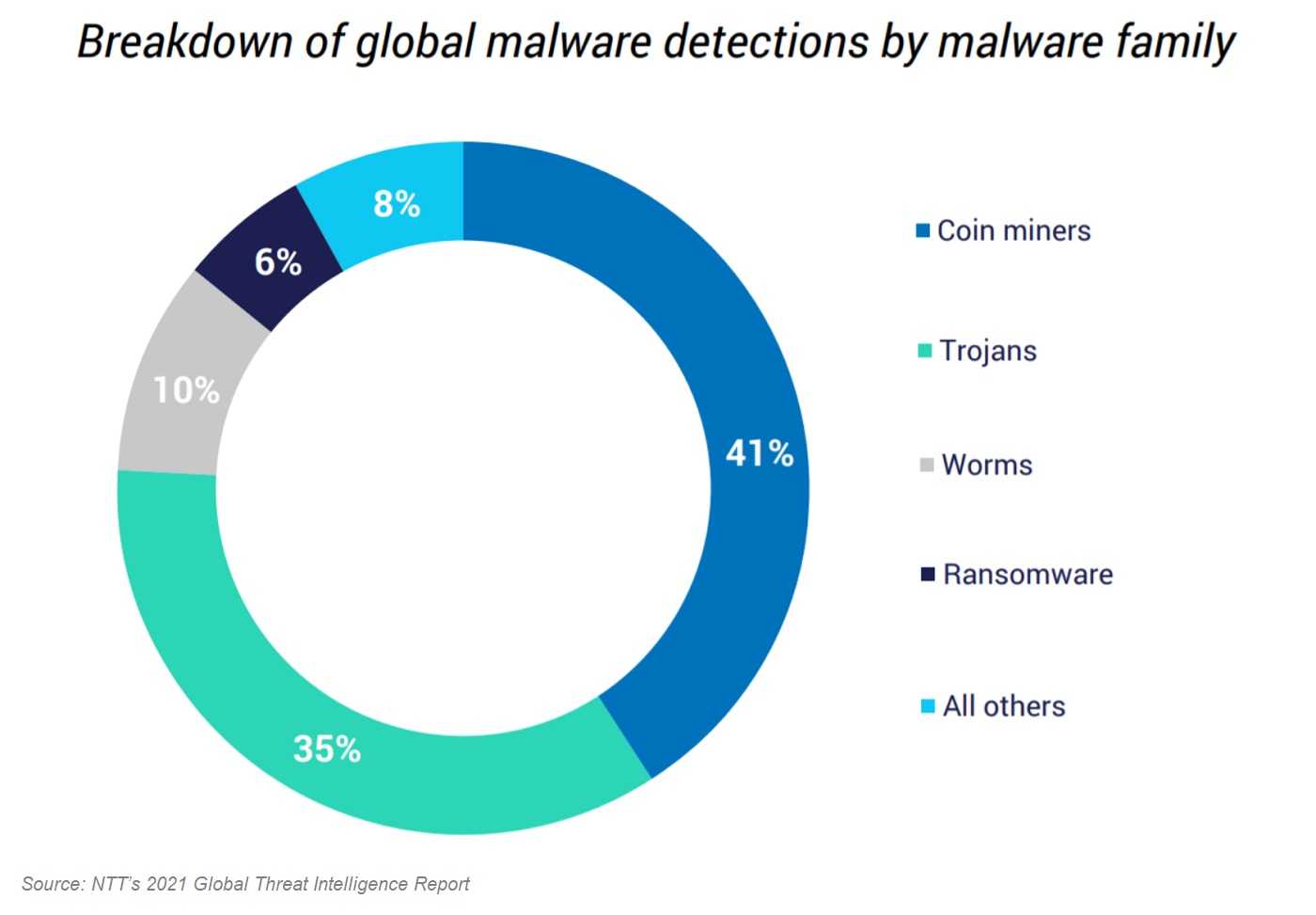
Since the advent of cryptocurrency, the act of cryptomining is necessary for those cryptominers looking for a payout. Cryptomining takes an enormous amount of power, and many miners find stealing it from another device is most helpful with their goal. The power is used for mining cryptocurrencies like Bitcoin, and a successful cryptominer gets a financial reward which is often paid in cryptocurrency. The downside for crypto-victims is finding their device is running unusually slow, with no idea of why it’s happening, and the device could eventually be rendered useless beyond repair.
Stealing a device’s power is called cryptojacking or the way miners enter a vulnerable system. Autom’s recent improvement affects the widely used Apache Log4j, an active zero-day vulnerability for Java-based logging libraries. The weaponized Log4j can evade security measures and execute the malicious code used against vulnerable systems, allowing for an entire system takeover.
Fight the Power-Stealers
Late last year, Apache released new patches to contain the Log4j flaw. User’s need to be aware of how well, or how poorly, their device is functioning. If there’s any sign of it running unusually slow and taking more power than usual to run, it’s time to do a reality check.
The real Boogeyman could be a cryptominer who’s cracked into the device and is draining its power for their own benefit. Even the issue is ignored, and fingers are crossed, it’s not likely to go away. It’s time to alert the IT department if it’s work-related, or have the device checked by a trusted tech source. Device awareness can be the first step to stopping cryptominers like Autom and others from further abusing your device and also rescuing it at the same time.

