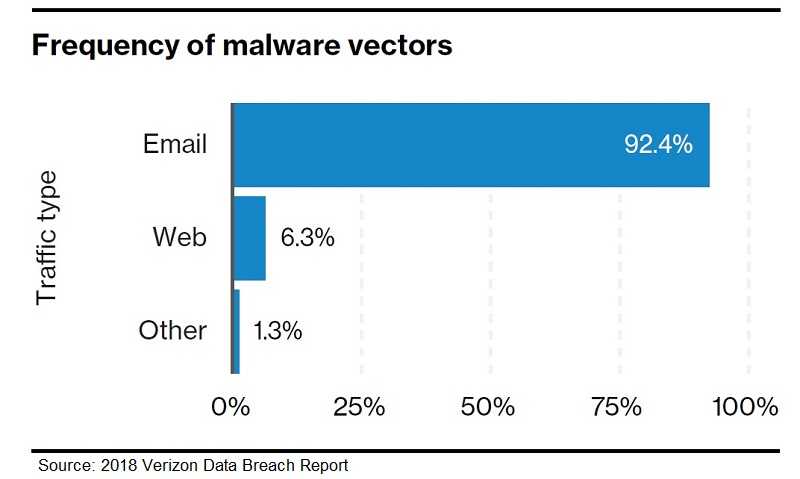
Of the 1,450 incidents it studied, 381 resulted in confirmed data disclosure and 59% of them were financially motivated. While 78% of the people studied never fell for phishing, 4% did. It’s that small percentage that counts. It only takes a single person to cause an organization to be compromised.
The term itself is common, but there are variations of it and any of them can be used in many types of attacks. The general term phishing is what most people think of and true, it is the over-arching term for the others. But they are not interchangeable. Phishing in the broad sense is when a criminal creates something, most often an email message that is designed to influence the recipient to click a link or attachment. In some cases, it may send them to a malicious website. The message can appear to come from anyone: A random organization, a colleague, a vendor, one’s mother, etc. Sometimes, they appear to be sent only to a single target and others they are sent out en masse in spam campaigns. In other words, they try to “bait” the victims. However, there are other deviations.
Spear Phishing
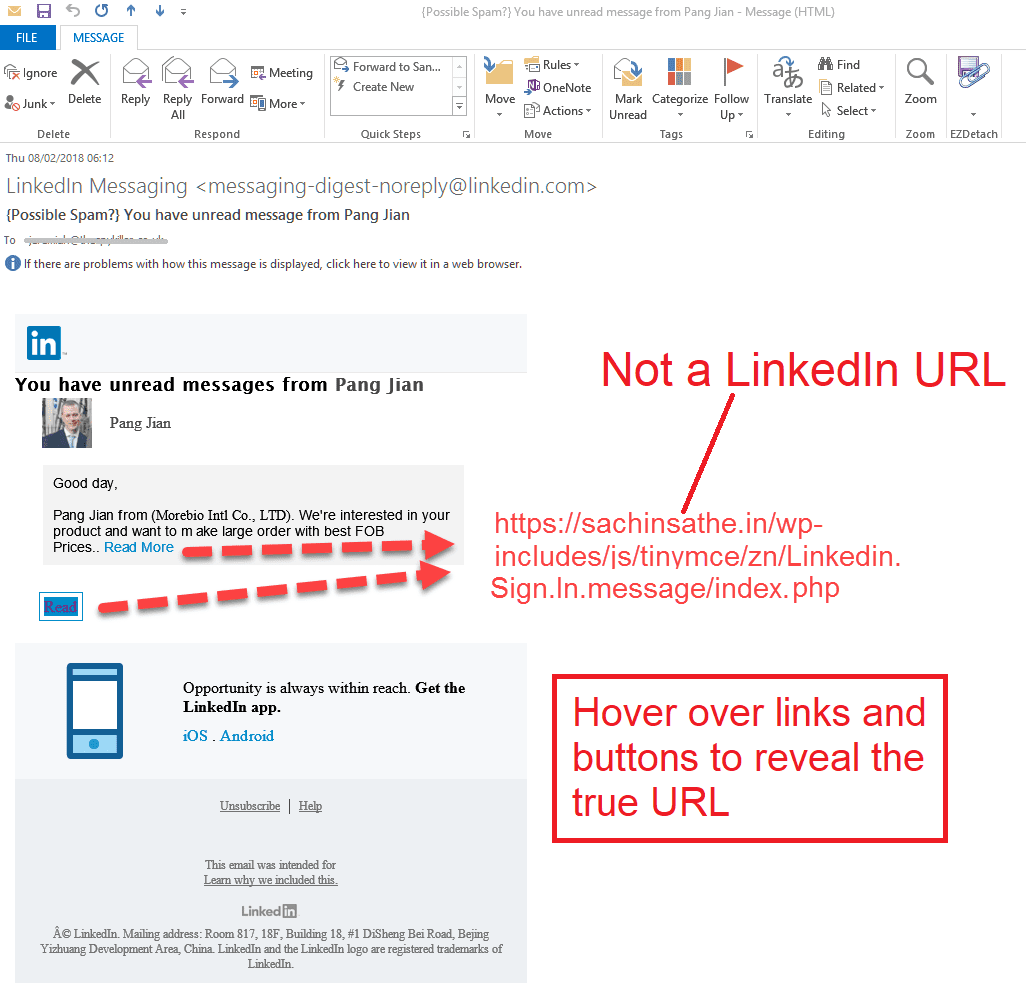
Spear phishing is when the criminal will actually pick a target and do research to find out about that person, persons, or organization. This information is then used to customize the email to make the email to appear as if the person or company sending the email is a known entity. For example, the business networking site, LinkedIn is often used as a research platform for these scammers. People put all kinds of specific information on there, such as their titles and roles, their skills, and dates of employment. And of course, their colleagues are often “linked” to them too. They use this information to send email to someone in the human resources department, for example to try to get W-2 information. They could also find out the name of someone in payroll, spoof the sender’s address and ask employees to click a link to verify direct deposit account details. The main difference with spear phishing is that targeted and very detailed approach the criminals take.
Vishing
This is phishing or spear phishing using a telephone. They may use a generic approach or find out details by viewing social media or other online profiles to use in a voice conversation. A very common vishing scam is the tech support scam. Someone calls to pretend they are from Microsoft, and more recently Apple, telling the victim they have a problem with their device and offer to help…for a small fee of course. The assumption is that nearly everyone has some type of issue with a computer and the criminals try to be the knight in shining armor to save the day.
Another one occurs during tax time in the U.S. The criminals call claiming the IRS is after you and unless you call them back and provide a payment card to pay a fine, you will be arrested.
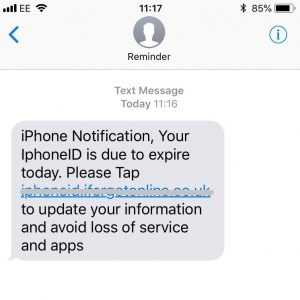
Smishing or SMS Phishing
Most of us have a mobile device that can send and receive text messages. Now, it’s becoming more common for the cybercriminals to use that for phishing attacks. They will send out text messages with links hoping the recipients click them. Often, they will appear to be from a financial institution or payment service such as PayPal or Venmo asking the recipient to click a link to verify details.
What is the risk of links and email attachments?
Depending on the goal of the cybercriminal, clicking on a link or opening an attachment can lead to a variety of security issues. In some cases, they are after login credentials to corporate bank accounts or personal information such as social security numbers.
In other cases, they may want to compromise the device. Clicking on links or attachments may take you to a malicious website. Once there, malware can be immediately installed without you having any idea what is going on behind the scenes. These sites are often so realistic that even the most experienced cannot detect they are fake. These sites may also be designed to exploit a vulnerability on the system. Security vulnerabilities seem to appear in Adobe Flash nearly every month. These are often used in attacks.
One other type of attack also uses malicious websites. The phishing email may contain instructions to visit a particular site to update your profile, for example. Sometimes, it may appear to be from someone in the IT department asking you to update your passwords or apply a security patch. The instructions may direct you to a website where you click on something to do the update.
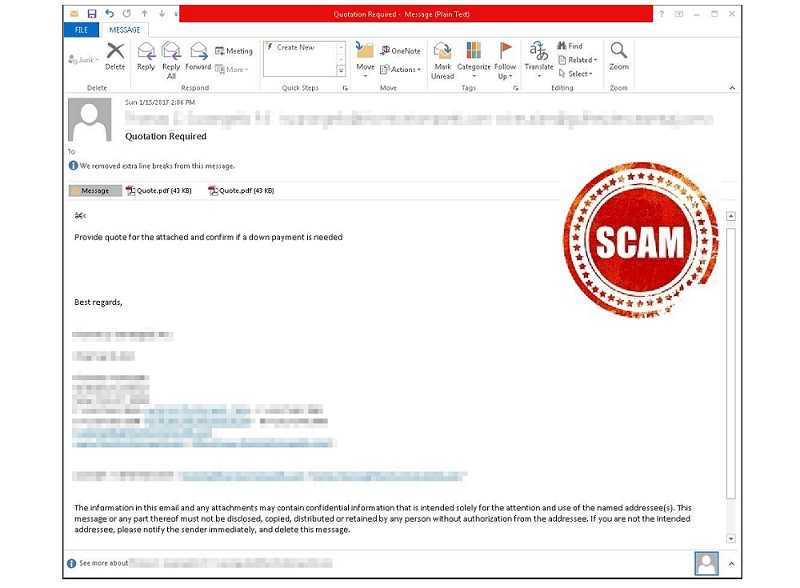
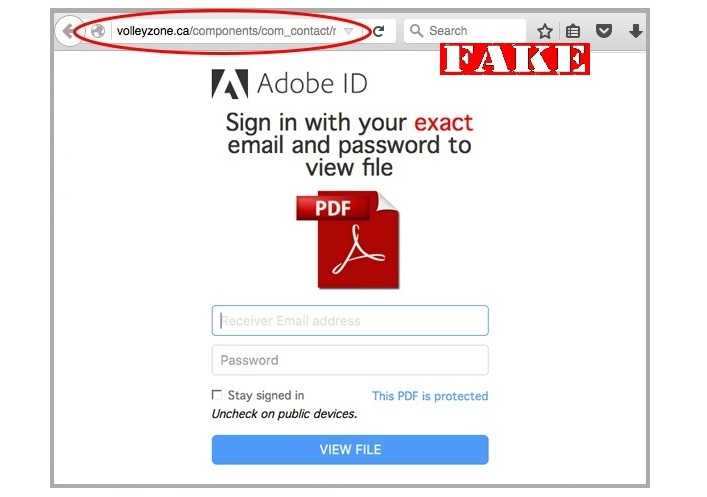
These days, a malicious attachment can literally be any type of file: PDF, .exe, .docx, .txt, .mp3, .png. It doesn’t matter at all. And if your device isn’t updated with the latest security patches and versions, they can all be used against you in an attack.
The messages in phishing attacks may vary widely. However, the end goal is always the same—to trick the user into clicking on a malicious link or opening a malicious attachment and therefore giving up information or access. More and more often, you may never even know an attack is taking place.
What can you do?

Keep your computers and mobile devices updated with patches and versions that are still supported by the developers. Keep anti-virus installed and updated on your devices too. While updating is often done by the IT department or is automatic in an organization, it isn’t always. Check with your manager to find out if you are responsible for keeping it updated and make sure you do it.

Be aware of what comes across your mobile device in the form of text or short message. If you don’t recognize the sender’s phone number, don’t click it. If you do, but it seems odd, give them a call and confirm they intended to send it.

Always confirm any requests that come in email from managers or IT personnel to perform a function such as update software, login into an account using a link, or wire money, before doing so.
Verify links you receive before clicking. You can verify where they go by hovering the mouse pointer over them or by holding down for a few seconds (on mobile devices) to see the entire link. Pay attention to the site names. If it starts with a number, don’t trust it. If it isn’t going to the official site, don’t click it.
Here are some commonly used links used to trick users into thinking they go to real sites. Pay attention to how closely some of them resemble actual websites:
http://192.168.2.10/PayPal/Security/ (Never click a link starting with an IP address)
http://www.cbsnevvs.com (URLs can look correct by disguising the spelling. This example uses to letter Vs to create a W)
http://applesecurity.com (It is common for scam URLs to contain a legitimate company name in the URL)
Of course, even knowing all of this, it’s still difficult sometimes to detect phishing. But the very best advice is simply to avoid clicking links or attachments in email or text unless you are 100% certain the email is legitimate.

