Researchers from McAfee discovered a way that those on the “dark side” can send a Word document in email and although it is not malicious, it has the ability to disable the macro security settings on your behalf. They found that this document “downloads and executes malicious DLLs (ZLoader) without any malicious code present in the initial spammed attachment macro.” It disables the macro warning message, so you don’t know what is happening when the subsequent malware is hitting you.
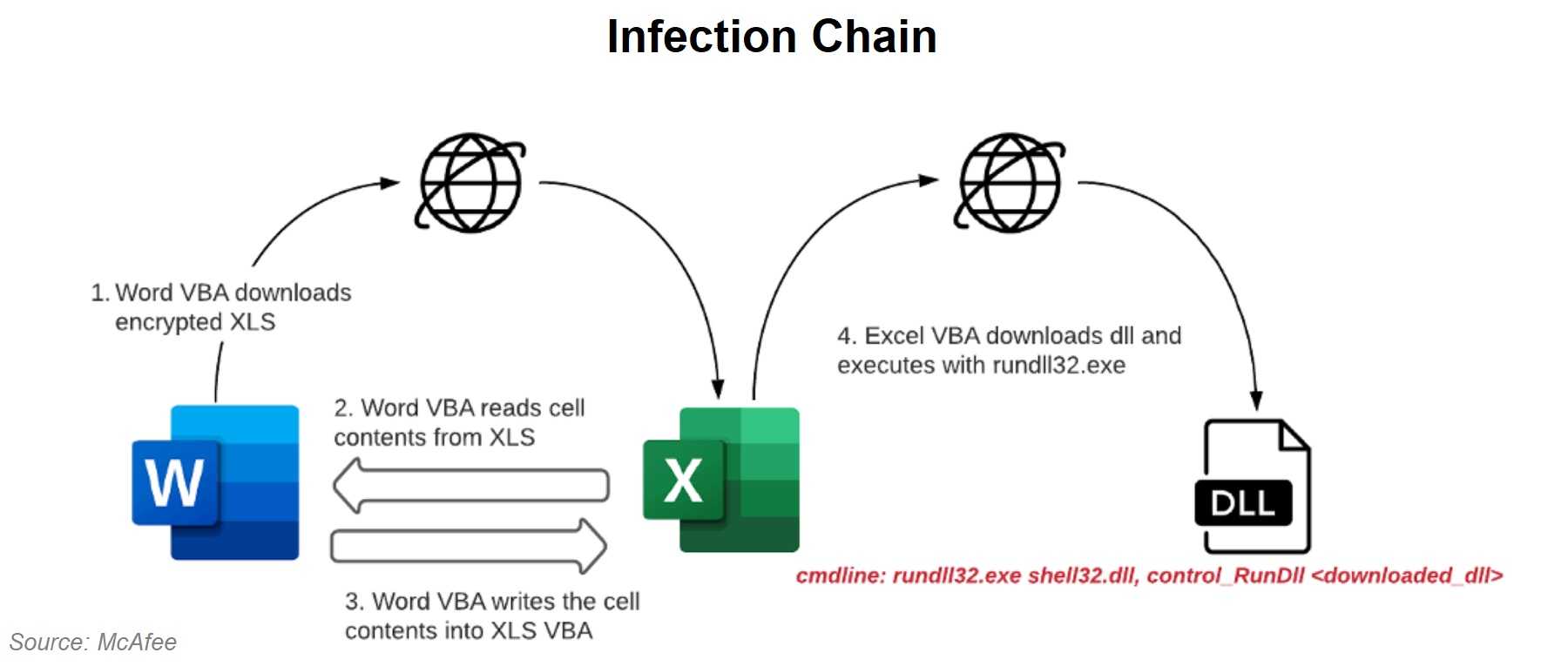

And keep these other phishing spotting tips in mind:
- If you don’t know the sender, don’t click it.
- If you are not expecting it, don’t click it.
- If you are not 100% sure any attachment or link is safe to click, don’t click it.
- Verify anything you might consider clicking with the sender using an independent means, such as a new and separate email message, a phone call, a text message, or a personal visit.
- Spelling and grammar count. If the message is a mess or unprofessional, it should be deemed suspicious.

