Blog/Vlog
Read our latest blog posts for expert advice, industry insights, and updates on the ever-evolving world of managed services and technology.
PayPal Credential Stuffing Attacks, 35,000 User Passwords Compromised
It looks like human nature strikes again. PayPal recently announced attackers succeeded with credential stuffing attacks on nearly 35,000 PayPal accounts. The widely used financial app notified its...
Is Cybersecurity Insurance For Me? What To Know
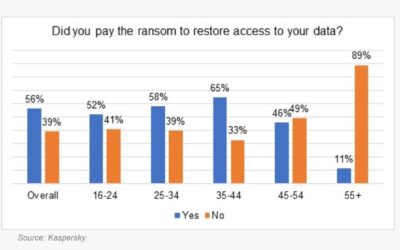
Cybersecurity insurance isn’t the foolproof antidote to cybercrime, but for the right person or business, it can make a lot of sense. Help with recovering from a cyberattack is something everyone...
Protecting Your Accounts Made Easier With 2FA And MFA
Keeping passwords safe from hacking has long been a challenge for most users, even though it can be the heart of staying safe online. Individuals and businesses alike struggle to keep accounts safe,...
Children As Online Targets-What Every Parent Needs To Know
Adults should be well-aware of hacking and the risks involved when traversing online. But what many don’t know is the sad truth that children are also targets of online abuse. Sadly, this includes...
Harbor Networks/HarborShield Cybersecurity has expanded territory and opens new Albany office!
Harbor Networks/HarborShield Cybersecurity is excited to announce that it has opened an office in the Albany Region to support its expanding client base. Harbor Networks a Managed Communications and...
Know When It’s Time To Hang-Up. Don’t Fall Victim To These New Phone Scams.
Just recently, it was discovered three new phone scams are making the rounds. These scams play on our fears (a scammer favorite), they’re tough to spot, and they’re after your money. It’s always...
WastedLocker Ransomware Sneaks In And Out, Bypasses Detection
In May of this year, the world discovered an effective and stealthy ransomware known as WastedLocker. A very public attack on Garmin navigation systems alerted the cybersecurity community to the new...
Tips to Avoid Social Media Cybercrime
We love social media these days. Facebook, Snapchat, Twitter, LinkedIn, and many others can lead to lots of sharing and fun, but also carry significant risks. This is particularly true now that...
FREE Windows OS 11 Download Includes FREE Vidar Info-Stealer Malware
It’s well-known that downloading apps and other software from unofficial sites, including social media outlets, is risky at best. Yet those who know better still do it for their own reasons, like...
Relentless Ransomware Strikes Making Healthcare Orgs Queasy
Hospitals and other healthcare organizations have long been a top target for ransomware attacks. Over time, this brand of cybercrime continues to grow rapidly, with stealthy upgrades made along the...
End Of Support For Internet Explorer 11 Browser
In case you missed it, the time has finally come to let go of your Internet Explorer (IE) browser. As of June 15, 2022, Microsoft has retired the IE 11 desktop application. In addition, certain...
U.S. Agencies Issue Advice On Countering Russian State-Sponsored Threats
New advice has been issued by the U.S. Cybersecurity & Infrastructure Security Agency (CISA), the FBI, and the National Security Agency (NSA) in countering the threat of Russian state-sponsored...
SMBs And Cybersecurity: Building A Strong Plan From The Ground Up
The data breach headlines normally focus on mega breaches involving huge corporations and their many customers. The reality is, many small-to-medium sized businesses (SMBs) suffer data breaches that...
Don’t Get Hooked Updating That Security Certificate
As if it isn’t difficult enough to determine if a website is legitimate or not, a new phishing technique is going to be keeping us all on our toes now. Cybercriminals are trying to trick website...
Tips To Stop Pesky Robocalls Without Using Third Party Apps
Oh, the never ending robocalls…morning, noon, night…surveys, telemarketers, vishing…For most folks, robocalls can’t stop soon enough. Data shows that in March 2019 alone, 2.5 billion illegal...
Malware Downloads From Harmless Word Document
You have heard it over and over and likely, your reaction is “Yes, I know. Don’t enable macros in Microsoft documents or spreadsheets.” Well, don’t plug your ears or turn away, but you’re about to...
Harbor Networks Guide to E911 and NG911 Regulations
Harbor Networks Guide to E911 and NG911 Regulations: Legislation and requirements around 9-1-1 are ever-changing, and businesses are responsible to ensure their telephone systems are compliant. New...
An Overview Of Several Types Of Phishing Scams
In this day and age, anyone who has an email address or even a telephone has heard the term “phishing.” It’s the most prevalent form of social engineering in existence. The latest Verizon Data...
New Autom Cryptomining Evasive Twist Leaves Devices And Victims Powerless
If cryptomining is a baffling concept to you, you’re in good company. In fact, most hackers count on victims not understanding the issue to ultimately help with their success. And now, a continuing...
What Is The Price Of The Average Data Breach? Awareness Training May Be The Key To Prevention
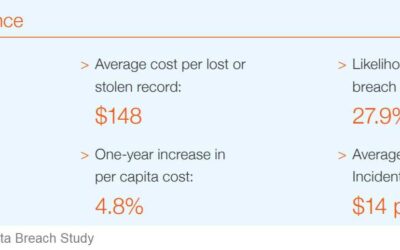
The price tag for a data breach went up this year, way up. Although the global average cost per breach is now a whopping $3.86 million, the average cost for the U.S. is $8.64 million, the most...